WP vs hackers: 5 hyper simple protections
During the winter 2020 my blog was hacked. I lost time and energy for nothing. Anyway thanks to that story, I checked the security of my blog and its breaches. I found 5 very simple protections. I think and I do hope that I'll not have any other problems with that.
February 2020. For a weird reason my blog is down. In fact it's redirected to an unknown website. It's quite easy to repair. You need to follow this guide on WP forum. As it's not redirecting to a porn website, I've put it on the next day task list. The always next day list... As I'm a famous procastinator I do not really care. But after one week, my backup is out of date and I don't have blog anymore.
Who could imagine that a confidential blog would be under attack? Not me. However we don't have to forget the smart guys who are using blind attacks to test or have fun. Like many people, 34% of websites1I use WordPress. Following the same paths than the viruses attacking Windows, bots are attacking WPwebsites. If only I would have had the 5 hyper simple protections...
It was not a big deal as I lost 4 or 5 posts. I was in Japan and I wanted to write about it... but I was lazy. Combined to a blog that was down I started to take care during the inter season. Now, everything is fine and I've learnt something new. It's very simple to be protected from those attacks. There are obvious step but I did not followed them.2.
HTTPS
We hear a lot about security and we think that our webhost takes care about it... Not necessarily. I was client from a very competitive Czeh webhost, wedos, but I would have had to change my subscription to have HTTPS3. The procrastinator won again and I did not do it.I take a look to other webhosts. I discover that LWSthe provider of my hostname has the option in its basic formula and you just have to activate it.
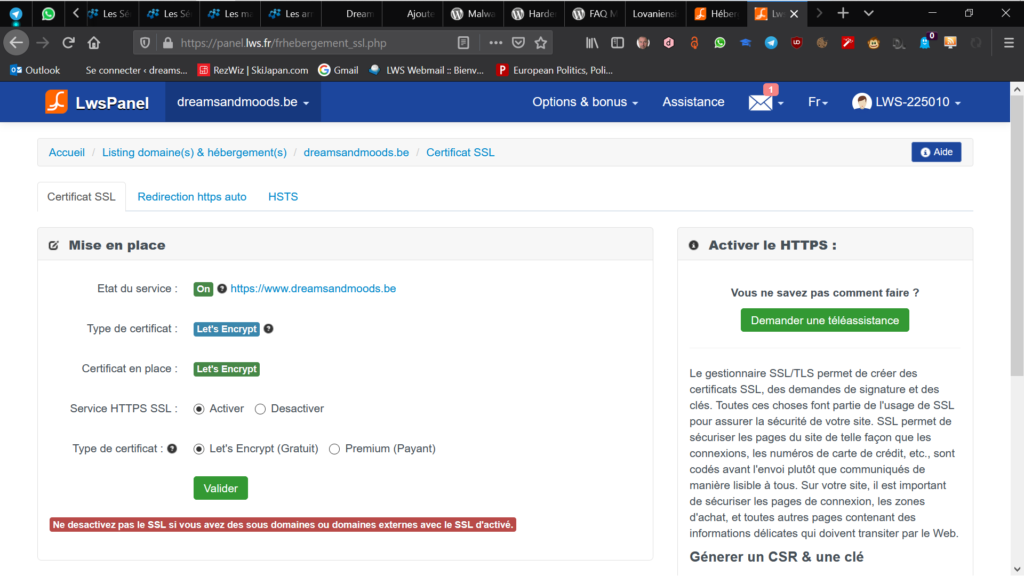
Once you have the certificate from your webhost, you only have to come to your command center in Wordpress and add https in front of the name of your website.
Be up to date
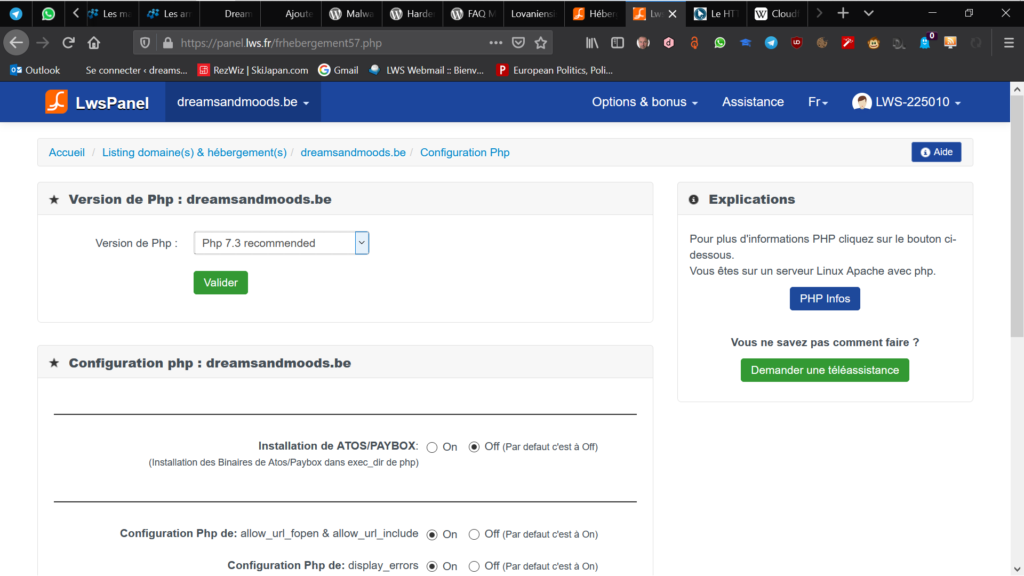
This part may be seen as stupid because it's obvious that the core of WP and the extensions have to be up to date. I automatized it. It's simple and efficient. I use colormag a well known template and the usual plugins such as Akismet or Jetpack. But I was not up to date: PHP4 and my data base MySQL. I do not think that it was the entrance of the attack but it's better to take care of everything.
Address the weaknesses of WordPress
As I said, WP is very popular and very simple. Even if safety is a main point, there are to weaknesses to eliminate
admin
The "basic" user is the administrator under admin. You have to change it quickly. If you do not change the default log "admin" a corrupted password gives the access to your website. To change that, go to users, create a new one and give him administratorrights and then erase the default admin.
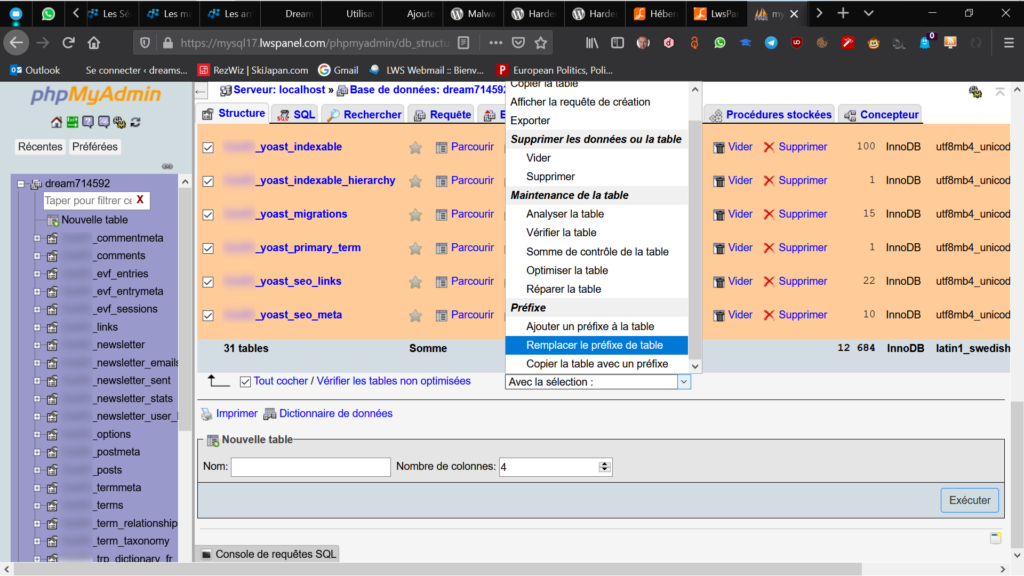
MySQL tables prefix
Even if this subtitle might be seen as complicated, it's very simple. Your database will receive several files from Wordpress. By default, they are named as:
WP_commentmeta WP_comments WP_options etc.
WP has to be rename to any other prefix. To change it you have a very simple manipulation. You enter PHPMyAdmin, you enter the database and then you activate select all in structure and in the rolling menu with selection you'll find replace prefix in the table. You chose a prefix and it's done.
With these two manipulations a traditional attack wil be pushed away without any effort.
Captcha
The idea was suggested by LWS.Sometimes it annoys me but I kept it: a captcha on the login page. The Login No Captcha reCAPTCHA extension is perfect for that job. When you connect to your site you have to proof that you are not a robot. Sometimes I think it's a bit too much, but at the end I have to say I'm OK with it.
Cloudflare
At our blogger level Cloudflare is a web security service against brutal attacks. Wikipedia gives more information and my description is clearly simplist. Yet the free version may use the redirection through their servers while being scruted against attacks. You only have to creat an account and change your DNSparameters. I try to make it simple: the Domain Name System helps to retrieve your website with its name. Instead of having your webhost doing the job, you ask Cloudflare to do it. At the same time it has an eye on the ones who are searching for your address.
It's the same as if the postal service would ask a security company to deliver your mail. Your home is safe, nobody can approach, but you can still be delivered a pizza.
Nicolas Boucher (who is laughing about this stupid metaphor. Purists may rebel!)
I do think that with these advices, most of the attacks would be pushed away. You can find other useful tips on hardening wordpress. I lost a huge amount of time because of a basic attack so I do think that theses manipulations are more than welcome. Of course, don't forget to backup.
- information coming from kinsta.com kinsta.com [↩]
- I decided to write a post about it as I was visiting the LSO website: same mistakes were made. [↩]
- The most important with HTTPS it the warranty of the security of the users and the exchanged data. More info here here [↩]
- a web applications oriented language [↩]



